Only available on the Pro plan.
Overview
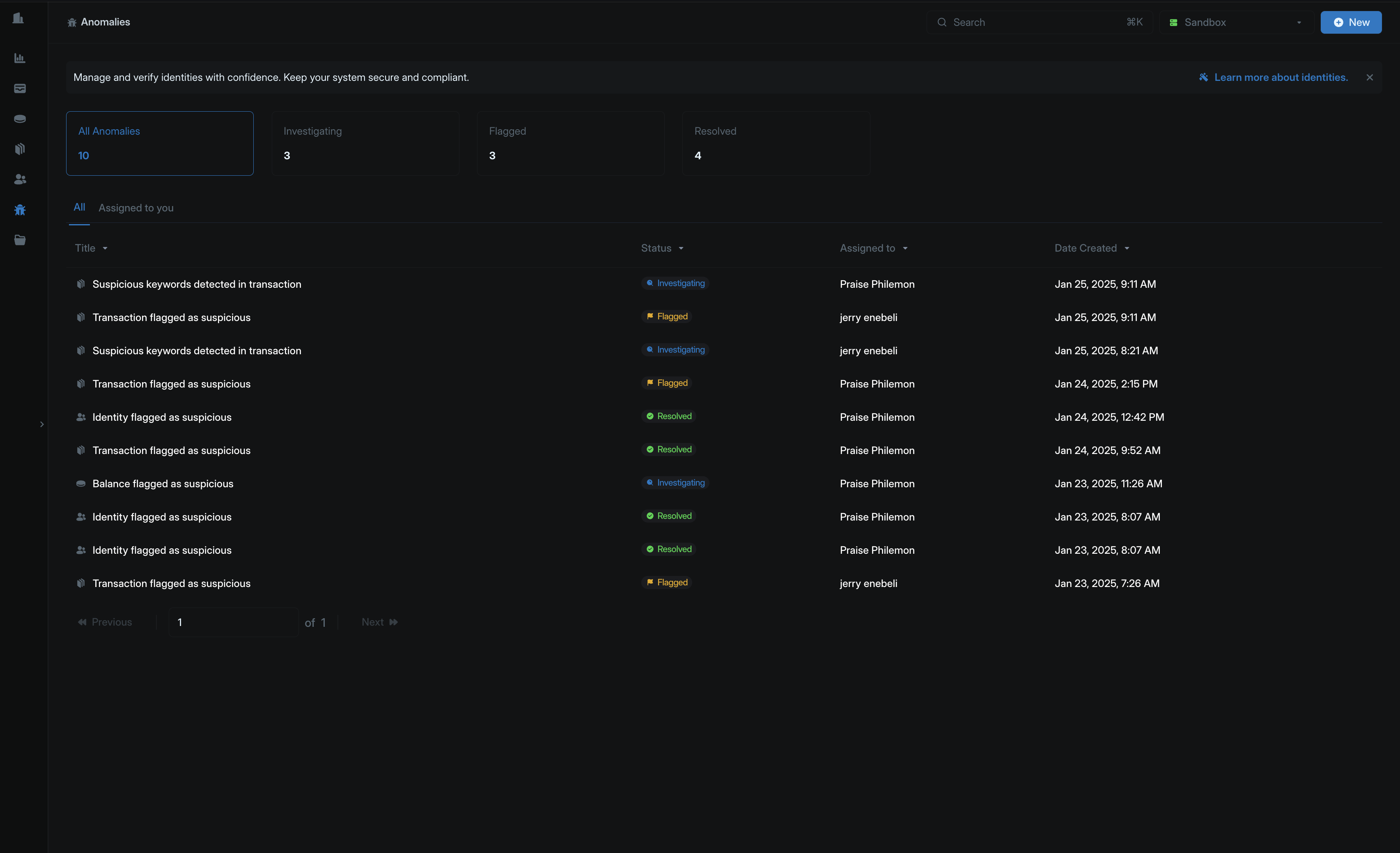
Anomalies help you monitor your financial data, flag suspicious activities in real-time, and notify you to take action. Blnk currently flags anomalies based on pre-configured rules built into your Cloud workspace.Anomaly types
There are three anomaly types — balances, transactions, and identities.Balance anomalies
These anomalies are flagged when suspicious activities are detected in one or more balances.- Increased credit/debit frequency detected: Frequent unexpected credit/debit transactions above normal activity patterns may indicate account irregularities or potential unauthorized access.
- Unusual repeated transactions: Repeated transactions with consistent amounts and timing that deviate from established patterns may signal automated fraud attempts or account tampering
Transaction anomalies
Transactions get flagged due to:- Suspicious time of transaction: Activity occurring outside established operating timeframes or expected business cycles warrants additional verification to ensure transaction legitimacy.
- Suspicious transaction keywords: Analysis of transaction descriptions identifies keywords associated with high-risk activities, suspicious patterns, or prohibited transactions.
- High-risk locations: Transactions involving jurisdictions identified as having elevated financial crime risk or inadequate compliance frameworks require enhanced scrutiny and additional due diligence measures.
Identity anomalies
Identities get flagged due to:- PEP or sanctions list match: he identity has matched against records in politically exposed persons databases or international sanctions lists, requiring verification and review.
- High-risk locations: The identity is associated with a jurisdiction designated as high-risk, necessitating additional verification steps and enhanced due diligence procedures.
- Unusual activity by senior customer: Unusual transaction patterns or account activities are detected on accounts belonging to elderly customers, triggering enhanced monitoring protocols.
Anomaly statuses
There are three anomaly statuses:FLAGGED
- The system creates an initial notification requiring investigator review.
- Each flagged case enters a queue for assignment to the investigative team.
- Automated alerts are sent to relevant compliance personnel.
INVESTIGATING
- An assigned investigator begins analyzing the full anomaly trail.
- The system tracks all investigative actions in a detailed audit log.
- The case handler documents findings and evidence during review.
RESOLVED
- The investigation concludes with a formal determination.
- All required regulatory reports are filed if suspicious activity is confirmed.
- The final case report documents actions taken and resolution details.