1. Sign up or log in
To access Blnk Cloud, visit cloud.blnkfinance.com.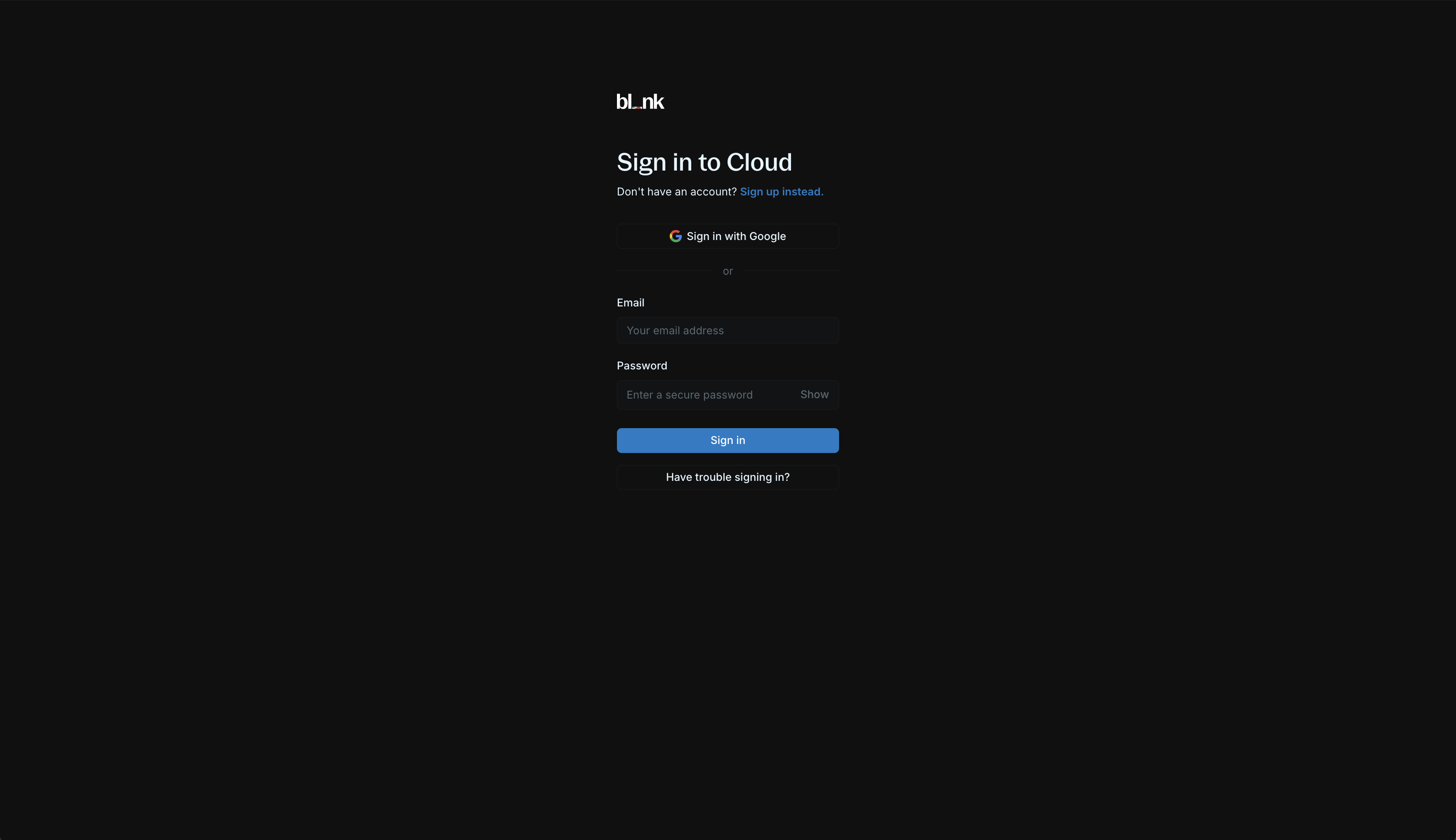
For existing users, sign in via Google or with your email and password.
2. Workspace setup
To complete your account, you need to create and set up your workspace.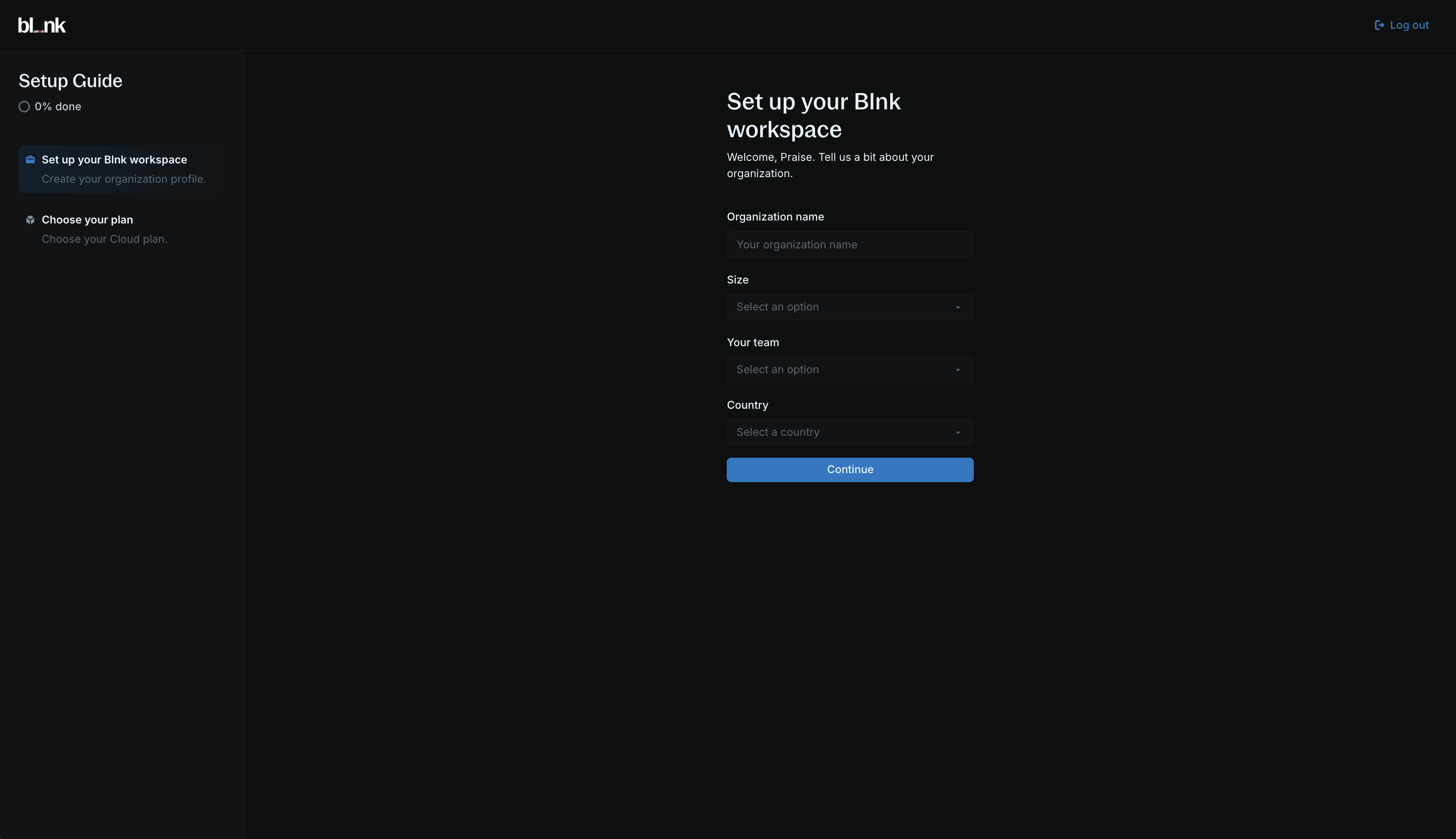
1
Create your organization
Enter your organization’s information:
- Organization name
- Team size
- Country
- Team
2
Select a Cloud plan
Select a Cloud plan that fits your needs to complete your setup and enter your workspace.You can choose from our 3 plans: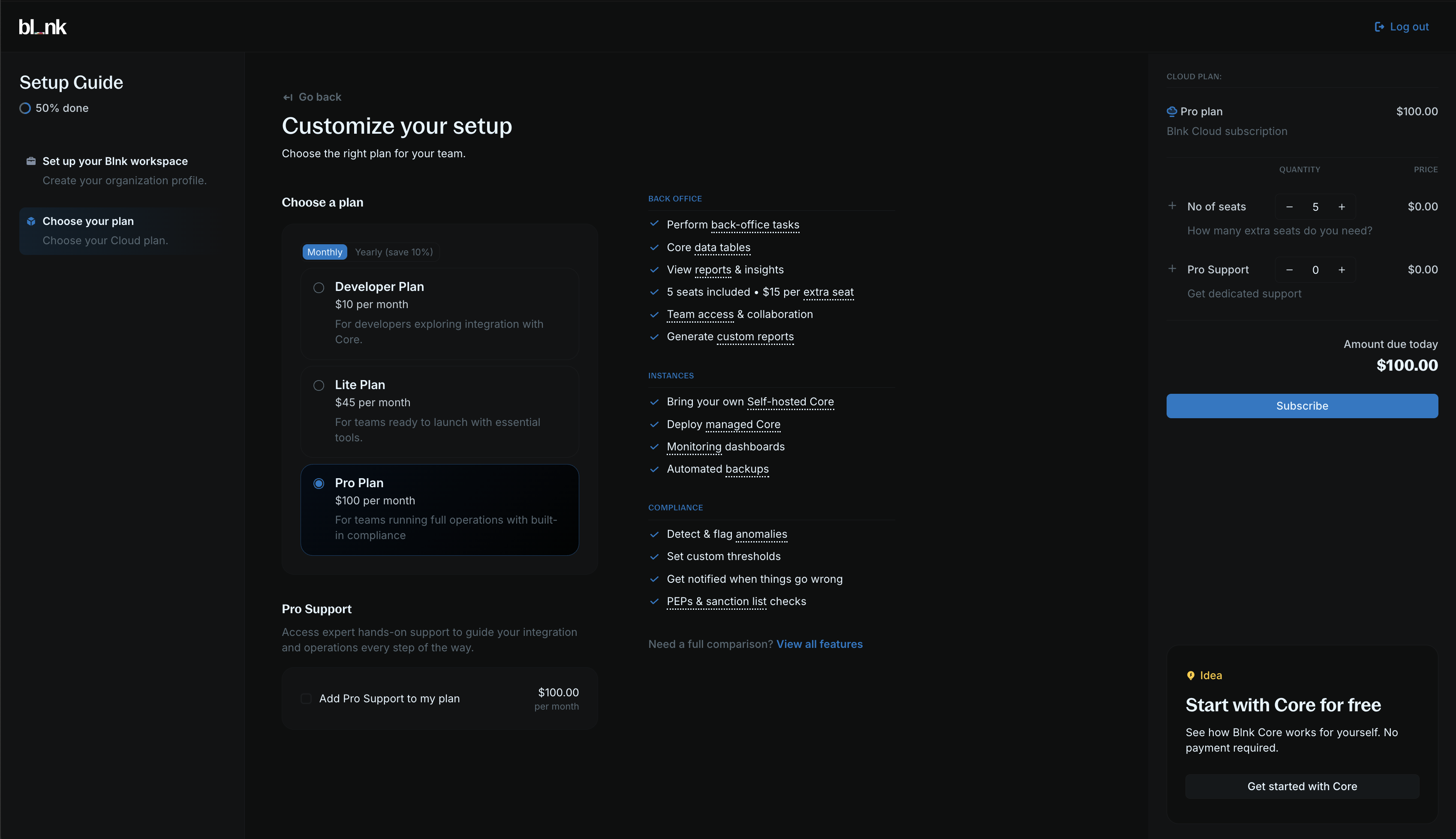
- Developer: Gives you read-only access, 1 seat and 1 instance.
- Lite: Gives you back-office operations, 2+ seats and unlimited instances.
- Pro (Recommended): Gives you custom reports, transaction monitoring, 5+ seats and unlimited instances.

To learn more about our plans, visit our Pricing page.
3. Deploy an instance
For Cloud to work, you need a running Blnk Core instance. You can deploy a managed instance on Blnk Cloud or connect your self-hosted instance.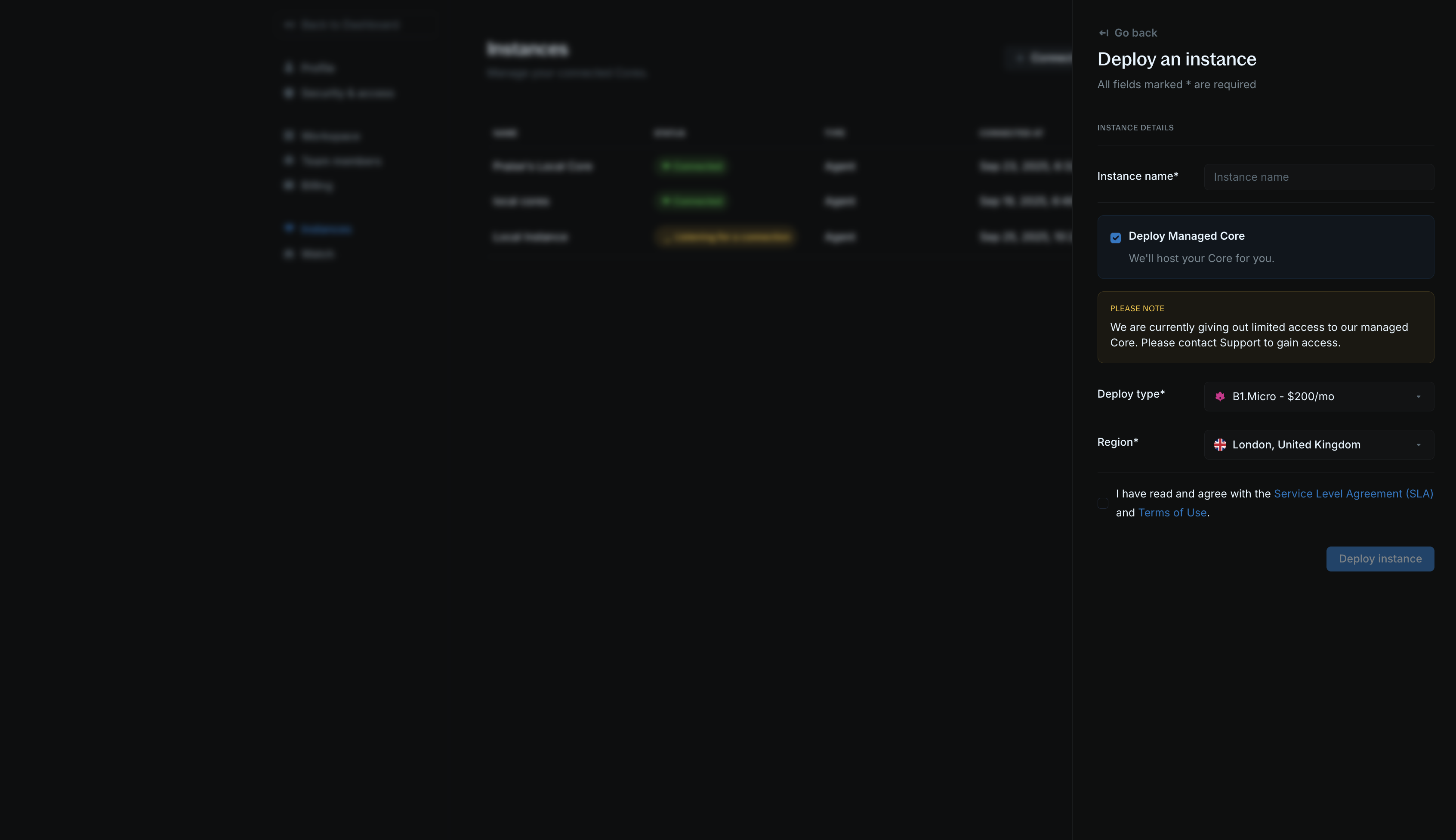
- Click Deploy new Core from your homepage.
- Choose a descriptive instance name for your instance, e.g., “Production”, “Staging”, etc. Any name works.
- Select your deployment type (B1.Micro and B1.Standard are currently available).
- Select what region you want to deploy your instance to.
- Confirm that you agree with our SLA and terms of use.
- Click on Deploy instance.
Self-hosting your Core?
Learn how to connect your self-hosted Core to Blnk Cloud.